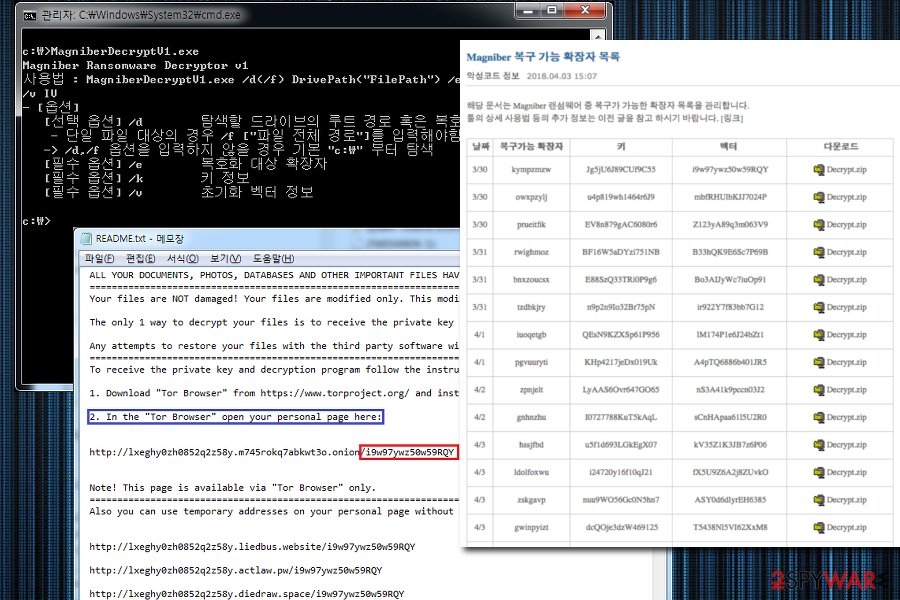
Clone via HTTPS Clone with Git or checkout with SVN using the repository’s web address. If you need to decrypt versions 1, 4, 5.0.1 through 5.2, then download and run our new tool linked below. The wait is over. For victims of GandCrab versions 1, 4 or 5, there is a new decryption tool available from Bitdefender Labs to help you get your life and your data back – for free.
- Distribution Method : Automatic infection using exploit by visiting website
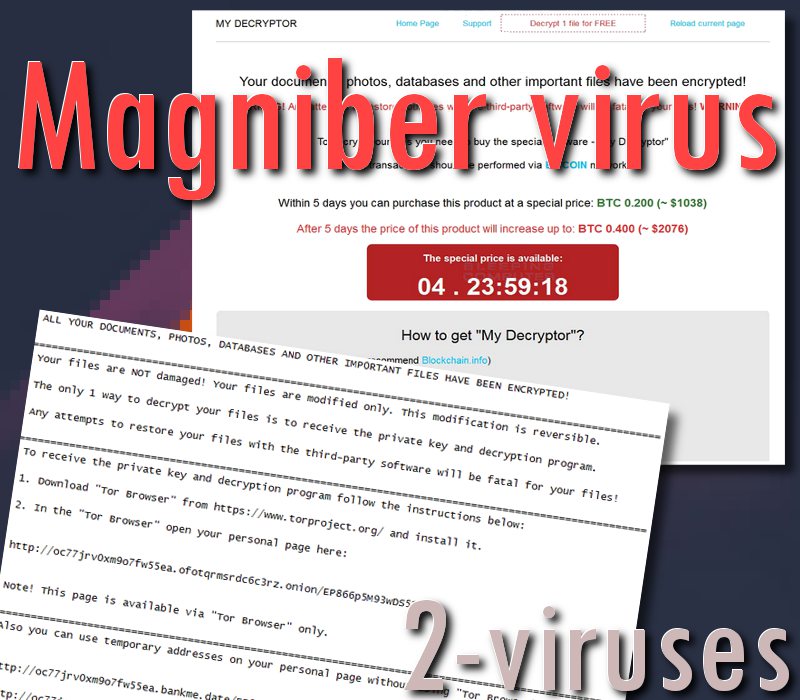
DECRYPT ME; Search for: The Week in Ransomware – January 1st 2021. DID YOU KNOW: 1 in 13 web requests lead to malware. @BleepinComputer, @AhnLabSecuInfo, @chum1ng0, @siriurz, @Kangxiaopao, @Jirehlov, @fbgwls245, @MShahpasandi,.
- MD5 : bdb30eefb423d7710d45501b2849bfad

- Major Detection Name :Trojan/Win32.Magniber.R216865 (AhnLab V3), Trojan.Win32.MyRansom.114880856 (ViRobot)
- Encrypted File Pattern : .ygshc
Ahnlab Magniber Decrypt V4
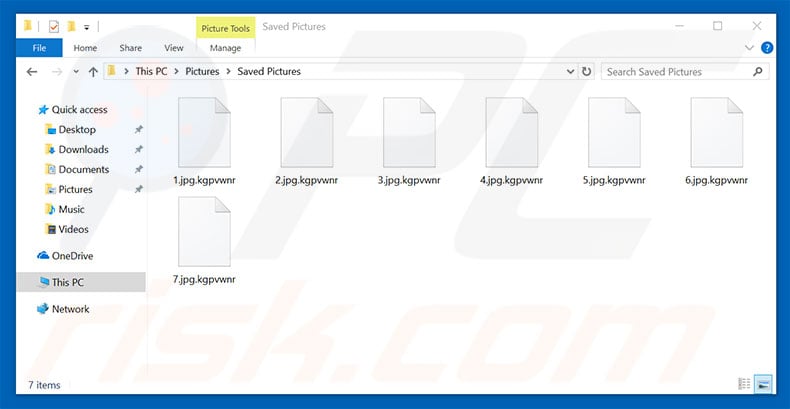
- Malicious File Creation Location :
- C:Users%UserName%AppDataLocalREAD_FOR_DECRYPT.txt
- C:Users%UserName%AppDataLocalygshc.exe
- C:Users%UserName%Desktop<Random>.exe
- C:WindowsSystem32Tasksygshc
- C:WindowsSystem32Tasks<Random>
- C:WindowsSystem32Tasks<Random>1
- Payment Instruction File : READ_ME_FOR_DECRYPT.txt
Ahnlab Magniber Decrypt V4.1
- Major Characteristics :
- Offline Encryption
- Only run on Korean operating system
- Change the default values of the registry entry 'HKEY_CLASSES_ROOTmscfileshellopencommand' and disable system restore (wmic shadowcopy delete) using Event Viewer (eventvwr.exe)
- Auto execute ransomware (pcalua.exe -a C:Users%UserName%AppDataLocalygshc.exe -c <Random>) and payment instrucition file (pcalua.exe -a notepad.exe -c %LocalAppData%READ_FOR_DECRYPT.txt) every 15 minutes by adding Task Scheduler entries
- Auto connect MY DECRYPTOR site (pcalua.exe -a http://<URL>) every a hour by adding Task Scheduler entries
